Identity propagation
One of the key advantages of using identity tokens in a microservices architecture is the ability to propagate identity. This means that once a service receives a token and validates it, the same token can be forwarded to other services in the chain of processing. This is crucial for maintaining a consistent and secure context throughout a multi-step transaction or workflow.
For example, if service A calls service B, which, in turn, calls service C, the identity token can be passed along this chain. Each service can validate and extract the necessary information from the token, ensuring that all actions are performed in the correct user context. This propagation of identity can be invaluable for auditing, logging, and implementing fine-grained access control across multiple services.
Practical workflow with Cognito
The following figure (Figure 6.10) shows the different steps involved in using identity tokens across components, as follows:
- User authentication and token issuance: The end user authenticates through Cognito, possibly using MFA for added security. Upon successful authentication, Cognito issues an identity token via its OAuth2 authorization server.
- API request: The client includes the identity token in the HTTP header when making an API request to a microservice.
- Token validation: API Gateway receives the identity token, then validates its signature and scopes to ensure it is issued by Cognito and contains the necessary permissions.
- Token propagation: If the token is valid, it is then passed to the computing layer (here, a Lambda function) running the microservice code.
- Exchange for credentials: The identity token can be exchanged for temporary IAM role-based credentials. These credentials are generated based on the identity context, as defined in the IAM roles assigned to Cognito’s identity pool.
- Resource access: These temporary credentials are used to assume the role they are linked to and interact with other services and AWS resources. The credentials allow for fine-grained access control, as they are linked to specific IAM roles with predefined permissions.
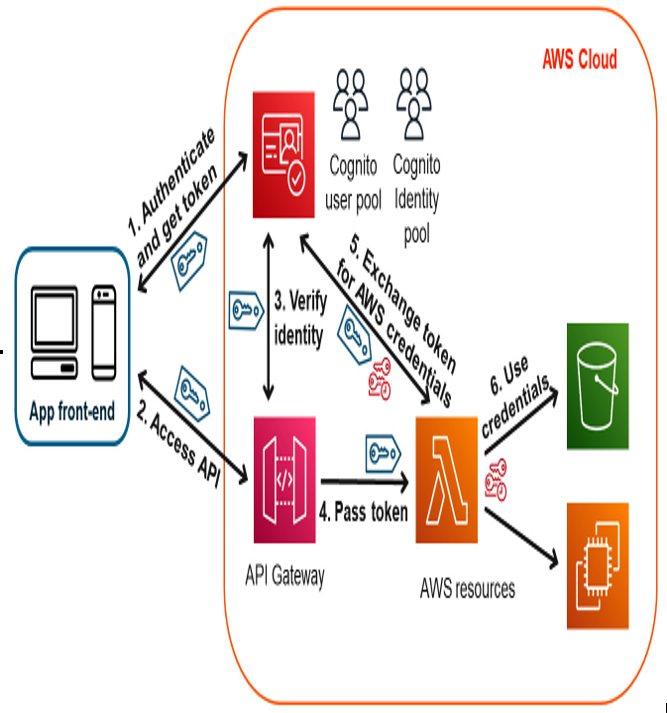
Figure 6.10 – Example using identity tokens and roles to access downstream resources
By integrating identity tokens with OAuth2 and leveraging identity propagation, you can build a robust, secure, and scalable authentication and authorization mechanism tailored for a microservices architecture.